Connecting to Amazon S3 Connection
Using IAM role and External ID (most secure)
For more information on External ID, please read How to use an external ID when granting access to your AWS resources to a third party.
Step 1. Begin S3 bucket configuration.
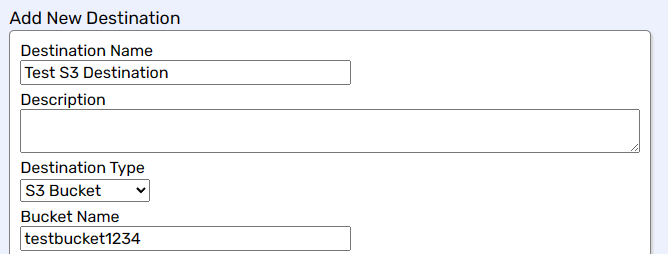
Enter Destination Name.
Enter Description (optional).
Select S3 Bucket from the Destination Type dropdown.
Enter your S3 Bucket Name.
Check Require External ID.

Step 2. Create IAM policy.
Open your Amazon IAM console.
Go to Policies, then click Create Policy.
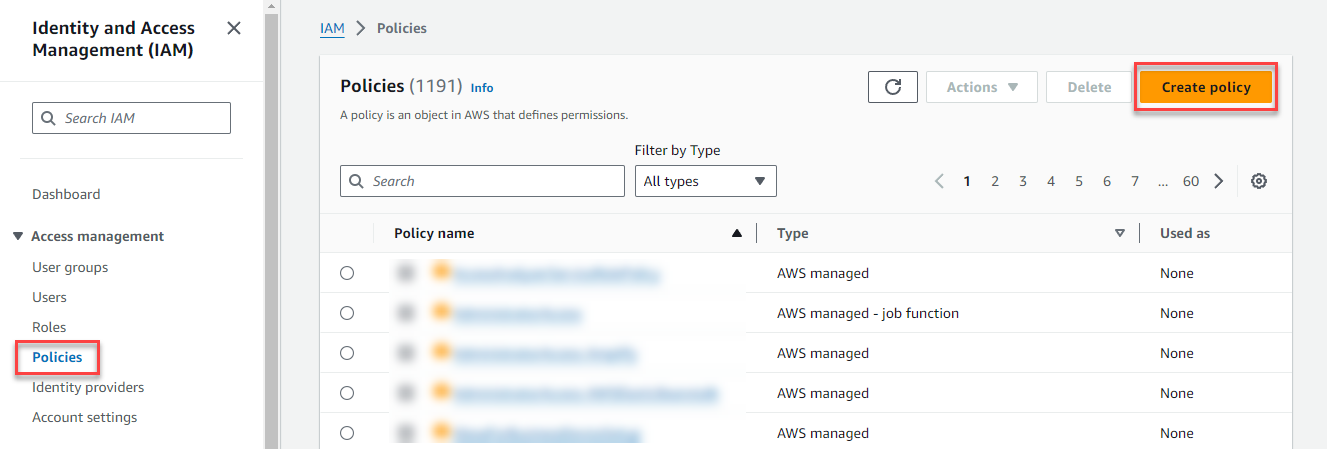
Select JSON tab.
Copy the policy from the Policy field.
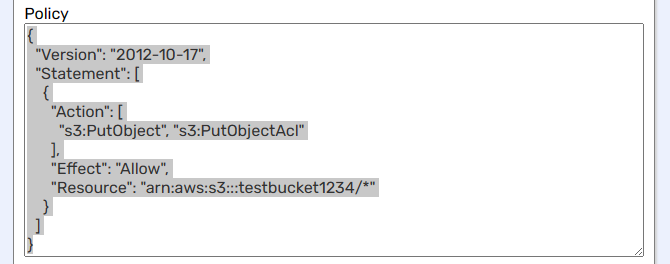
And paste it into the Policy editor.
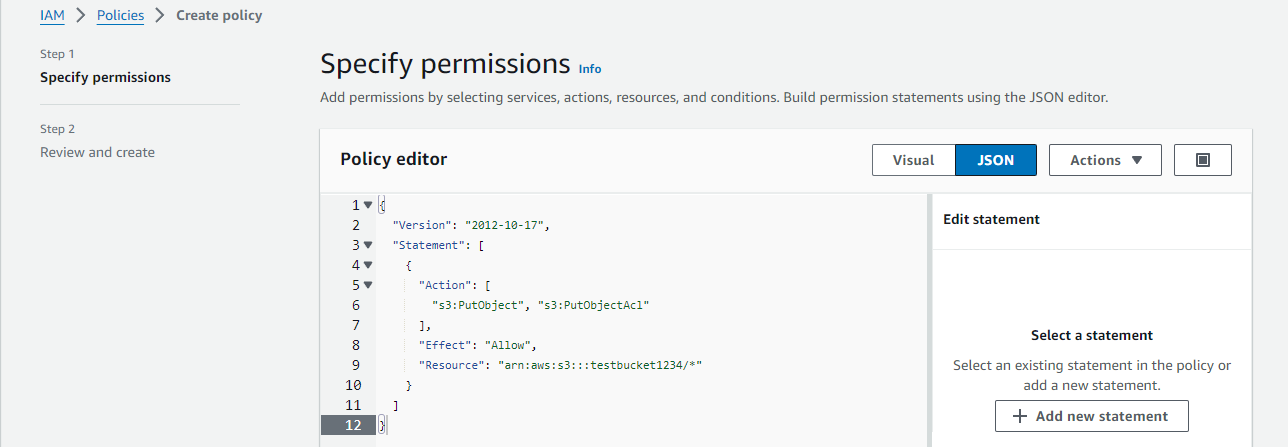
Click Next.
Enter Policy Name, for example Sequentum_S3_Access.
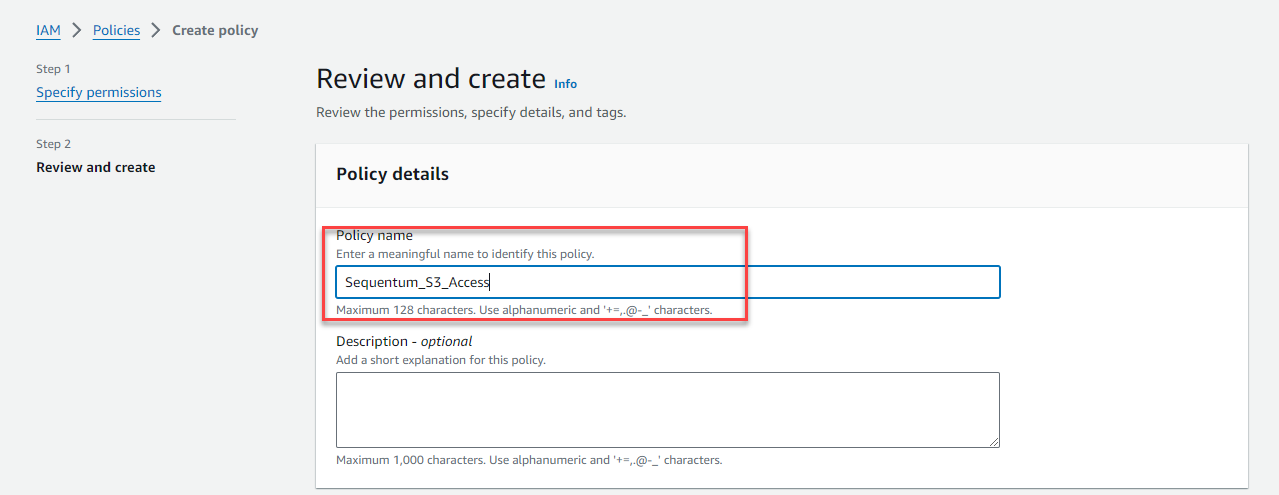
Finally, click Create policy.
Step 3. Create IAM role.
Find External ID and make a note of it. You will need it to create an IAM role in AWS. Please note that External ID is auto generated and you will not be able to change it.

Open your Amazon IAM console.
Go to Roles, then click Create role.
On the Select truted entity page, select Custom trust policy.
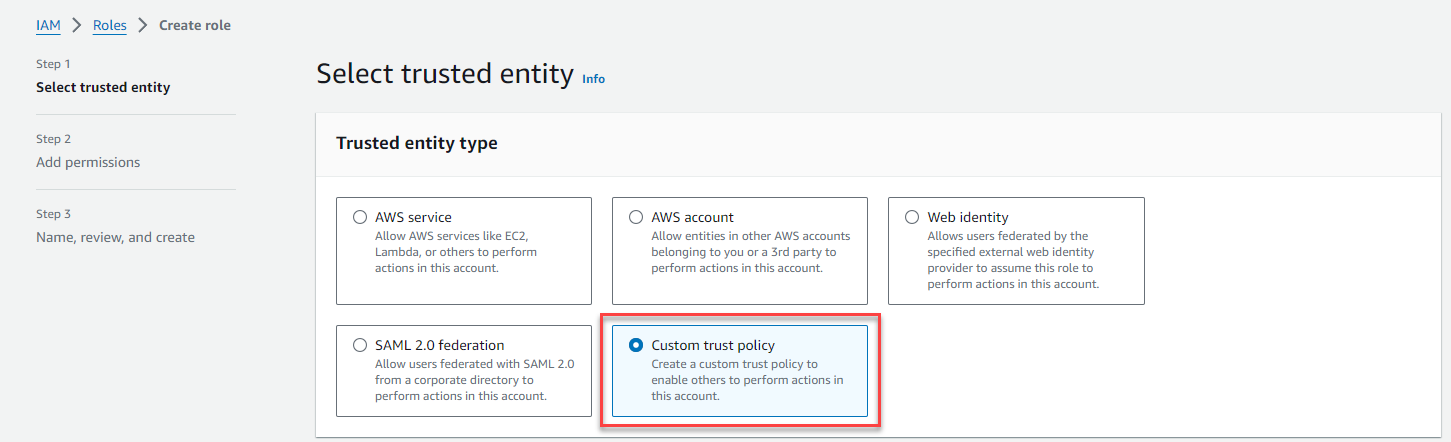
Copy the provided Custom trust policy from the Role Custom Trust Policy field.
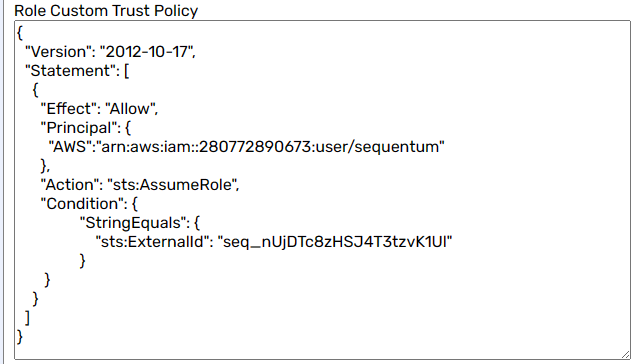
Paste the copied text into the Custom Trust Policy editor.
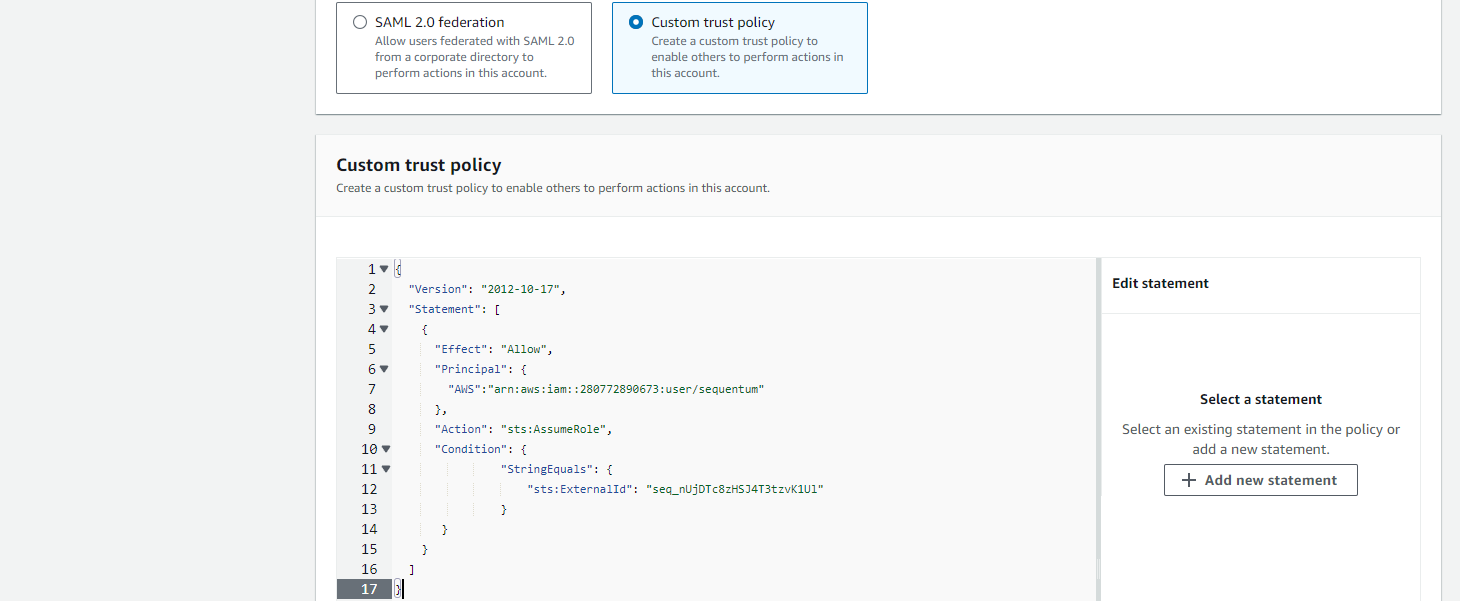
Click Next.
Find and select Sequentum_S3_Access policy you created earlier in Step 2.
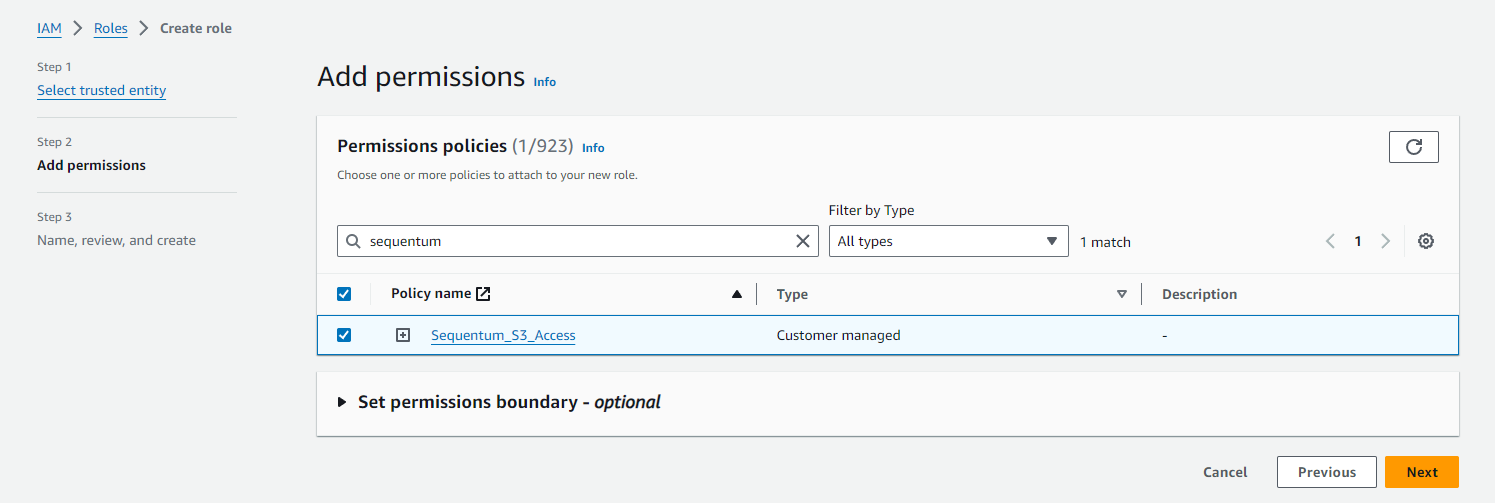
Click Next.
Enter Role Name, for example Sequentum_S3_Access_Role.
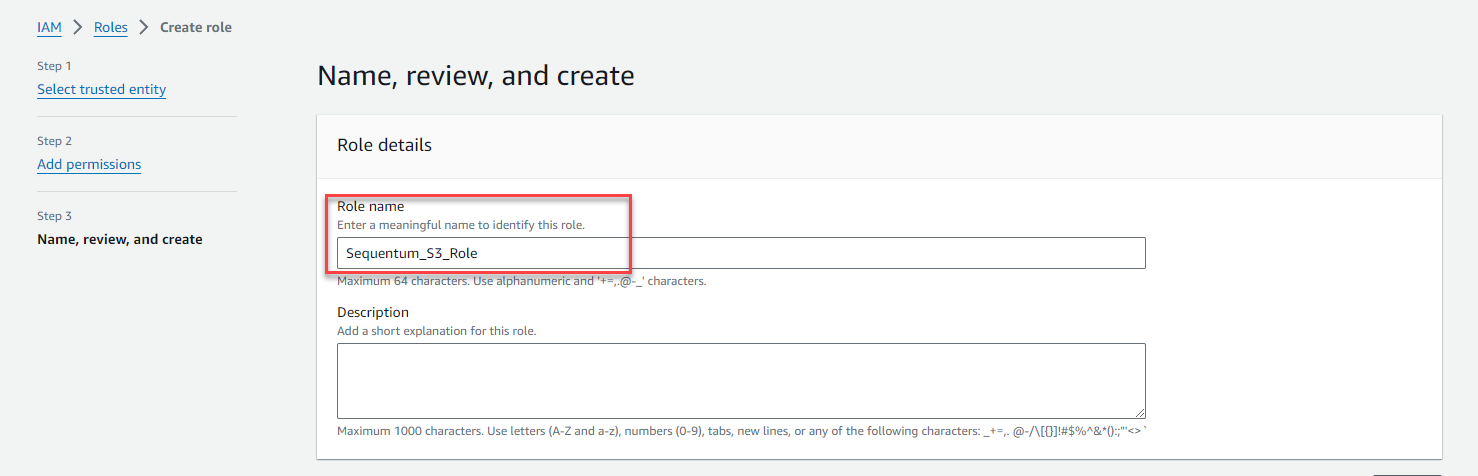
Finally, click Create role.
Click the Sequentum_S3_Access_Role role you created.
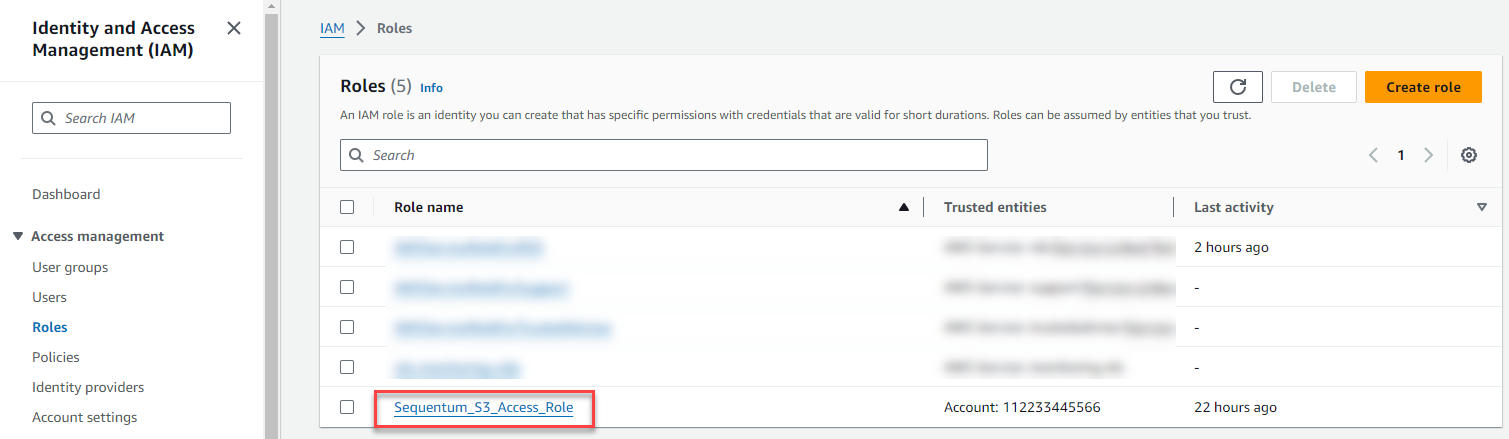
On the Summary page for the role, find the ARN value and copy it.
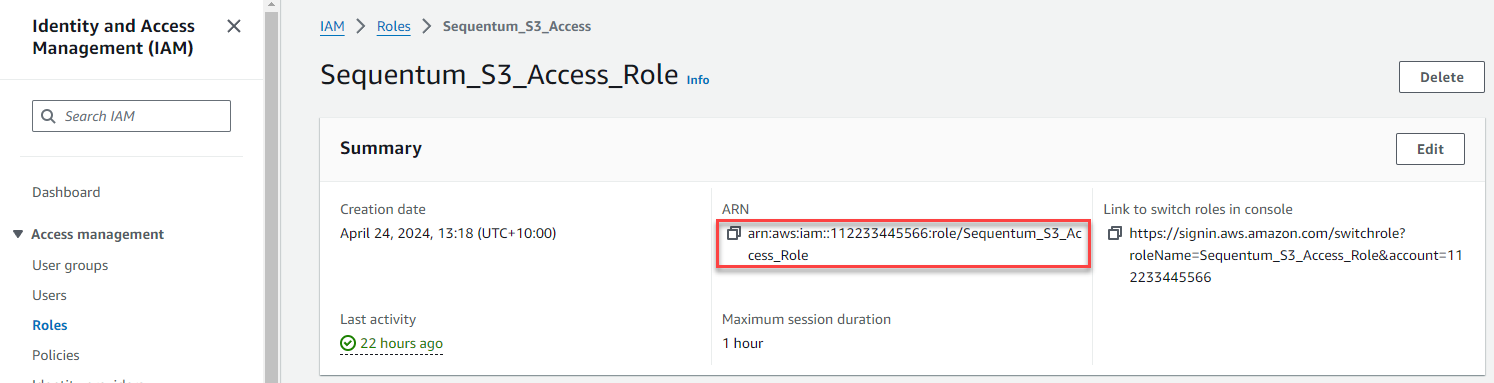
Paste it into the Role ARN field.

Step 4. Finish S3 bucket configuration.
Enter Folder (optional).
Click Test Connection.
Click Save.
Using Bucket Policy (less secure)
Simple Setup:
Copy and paste the generated policy into the “Bucket Policy” section of your S3 Bucket.
Advanced Setup:
If you have an existing Policy in your bucket you need to add a new Statement to the policy:
{
"Sid": "AllowSequentumGetObjects",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::280772890673:user/sequentum"
},
"Action": [
"s3:PutObjectAcl",
"s3:PutObject"
],
"Resource": "YOUR BUCKET ARN"
}Specifically, make sure the policy grants the Sequentum ARN permission to run s3:PutObject and s3:PutObjectAcl actions.
